Most companies don’t think they’re at risk for a cybersecurity attack until it happens to them. By then, it’s too late to stop the wheels already in motion. Their system is compromised, information may be stolen, and the entire organization is vulnerable. Prevention starts with business leaders creating a risk management strategy that ensures data and IT infrastructure remain safe.
A risk management framework isn’t as complicated as it sounds. By adopting this framework, your company is better equipped to assess and mitigate financial, legal, and cyber risks. After all, cyber attacks also affect your business partners, vendors, and customers.
Think of it as a type of insurance, providing you with control over your data and peace of mind should anything happen.
What is the NIST risk management framework?
The National Institute of Standards and Technology (NIST) is an agency of the U.S. Department of Commerce. This agency is responsible for creating the NIST risk management framework, a seven-step process that helps businesses manage their security and privacy. As a tool to keep the hackers out and your data safe, this framework can help protect your information and minimize risks.
In 2023, many businesses experienced cyber attacks such as ransomware and phishing. MOVEit, a file transfer application, suffered not one attack but a series of breaches. LastPass, a password manager platform, saw major fallout from an August 2022 breach that continued throughout 2023. T-Mobile, one of the most popular wireless carriers, servicing more than 110M subscribers, was hacked—twice.
No matter how big or small your company is or how long you’ve been in business, there’s going to be some level of risk. “At the moment, attackers benefit from organizational indecision on cyber risk—including the prevailing lack of clarity about the danger and failure to execute effective cyber controls,” write Jim Boehm and colleagues at McKinsey & Company.
Unfortunately, there’s no way to prevent breaches entirely. What you can do, however, is implement data protection precautions that make a hacker’s job that much harder.
Seven steps of the NIST risk management framework
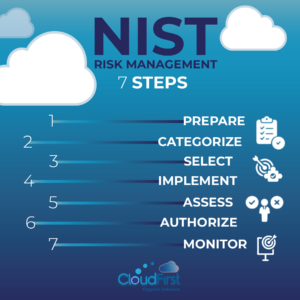
The good thing about NIST’s risk management framework is that it’s comprehensive and flexible for any organization to adopt. Even if your team isn’t familiar with the process, it’s easy to pick up and understand. If your business has an established security process and best practices in place, the NIST framework can easily complement the system you already use.
It also includes guidelines that meet compliance requirements of the Federal Information Security Modernization Act (FISMA). Take a look at the NIST risk management framework’s steps to understand how it works.
1. Prepare
This step lays the groundwork for the rest of the strategy. It starts with business leaders and executives opening communication regarding the framework.
For your team to effectively use the framework, everyone involved needs to understand each stage of the process and leadership’s objectives. From there, preparation tasks are often split into two groups: the organizational level and the system level.
At an organizational level, tasks typically include:
- Assigning key roles for overseeing the risk management framework.
- Creating the risk management framework specific to your business.
- Conducting any kind of risk assessment or updating previous assessments.
- Identifying and documenting common controls within your system. This may include security or privacy requirements.
System-level tasks might include:
- Identifying stakeholders who may be affected by and relevant to the system.
- Determining the types of information the risk assessment will process.
- Identifying privacy and security requirements necessary for the system to operate.
2. Categorize
The next step is to categorize your organization’s assets, data, and systems and ensure everything is accounted for. Once your team has logged your assets, you can see the big picture and, in turn, understand the potential worst-case scenario should any cybersecurity breach occur.
During this phase of the framework, companies can delegate who is responsible for the operation and management of each type of asset. Additionally, identifying each system’s intended use and how each will connect to the other systems within your organization is another part of the categorization phase.
3. Select
Controls are essential when developing a robust and reliable risk management framework. Security controls act as safeguards to protect the integrity and confidentiality of your organization’s system and data. Imagine a digital gate blocking out intruders. If your network becomes compromised, the countermeasures set in place can help protect your information and system. In some cases, these controls can even detect a potential breach before it happens.
In the most recent update of the NIST Special Publication 800-37, NIST specifically added and outlined privacy controls as part of its risk management framework. From a legal standpoint, laws now require organizations to establish data protection and privacy on behalf of their customers.
Privacy controls are often technical, administrative, or physical safeguards that protect personally identifiable information. These controls also need to comply with privacy requirements determined by the Office of Management and Budget (OMB). A person’s information, such as their name, address, or bank information, is the target of many cyber attacks.
4. Implement
Once you establish the controls, it’s time to put them into action.
During the implementation phase, organizations should install new processes and technology to help facilitate the risk management framework. Companies should also focus on testing the controls with the system’s security and privacy plans. This is where you see the framework in action. The strength of the controls is determined by how effective they are in preventing a breach of the system during this phase of the framework.
5. Assess
Next, assess the results of the implementation phase. The goal here is to determine whether the controls functioned as expected, performed effectively throughout your system, and produced the desired outcome.
Depending on the specific procedure your business has in place, assessments may be performed on an ongoing basis. Oftentimes this helps support the results of the implementation phase and helps you find weak spots to shore up.
6. Authorize
Once the assessment is complete, a member of the organization—usually a senior management official—determines if the security and privacy controls are effective and acceptable. This step typically involves a review of the authorization materials of the organization’s systems.
The senior leader determines any risks within the system, logs any failed controls, and approves authorization for the system to operate.
7. Monitor
With the risk management framework in place and the system in operation, continuous monitoring will help maintain effectiveness over time. You want to remain vigilant when it comes to the stability of your security and privacy controls. Monitoring how the framework performs allows organizations to frequently update security and privacy plans as needed.
A successful monitoring process may include:
- Creating management and monitoring processes across the organization.
- Establishing a risk assessment for potential changes to the system.
- Determining an assessment for selected controls.
- Reporting security and privacy risks to management officials.
How to use the NIST risk management framework

The NIST risk management framework is easily adaptable to any existing cybersecurity procedure your organization may already have in place, or it can serve as a launchpad.
NIST states, “Because the Framework is outcome driven and does not mandate how an organization must achieve those outcomes, it enables scalability.” Organizations can get started using the risk management framework with a few simple steps, such as:
- Start with leadership. Educate leadership teams on the framework process so they can have informed conversations, train employees, and delegate responsibilities surrounding the framework procedure.
- Establish levels of risk management. Organizing specific teams and management officials to oversee the implementation of the framework allows for more efficiency and effectiveness.
- Create profiles. By using profiles, which are essentially roadmaps, teams can easily identify problem areas and quickly troubleshoot them to improve the system.
- Prioritize and budget for cybersecurity. To set your company up for continued success, cybersecurity needs to remain a priority. This means setting aside the necessary budget for tools, technology, and third-party resources when needed.
As far as financial limitations go, because the framework is scalable, small businesses with limited budgets can utilize it just as well as a larger organization with a big budget. That’s the beauty of the entire process. The structure of the risk management framework supports your company at any level.
As part of a larger cybersecurity strategy, risk management provides an organized and systematic approach to identifying and managing risks. It helps break down tasks and responsibilities and supports a company-wide understanding of cybersecurity.
Protect your business with risk management procedures
Cybersecurity is a necessity for any business, no matter how big or small your organization is.
With so much information stored electronically, there is always a chance that information can and will be compromised. By implementing risk management frameworks at every level of your company, you can safeguard your data if your system is exposed.
Download CloudFirst’s eBook, The Business Leader’s Guide to Cybersecurity and Data Protection Strategies, to learn more about how you can protect your data, assets, and financial information.