Data is your most valuable asset. Without it, your applications are useless. That’s why it’s a prime target for bad actors looking to cash in. They know that if they can encrypt your data with ransomware, you’re likely to pay the ransom if you have no alternative.
Today’s companies need to do everything they can to protect their data. That’s why, at the COMMON POWERUp 2025 conference in Anaheim, California, CloudFirst’s Laurie LeBlanc presented an insightful session on ensuring data resiliency for IBM i.
This is what you need to know.
Why act now on data resiliency?

Cyber threats and ransomware are top of mind for virtually every CTO and CIO. This is true even on the IBM i platform, which is known for its stability and security. According to Forta’s 2025 IBM i Marketplace Survey, cybersecurity is the #1 concern across the board, with 77% of respondents citing it as a major issue.
When you look at what’s going on in the world, it makes sense to worry. We’ve seen a doubling of cyber attacks year-over-year, and 17% of those attacks are ransomware that goes after a company’s valuable data. The worst part is that, even if you pay the ransom, there’s no guarantee you’ll get your data back—26% of clients who pay still can’t recover their data.
If you can’t access your data, you stand a good chance of going out of business. Even for those who can recover, the average recovery period is 23 days—that’s over three weeks of IT downtime that leads to lost revenue, inflated costs, and reputational damage.
The picture gets even more complicated when you take into account the fact that 21% of threats are dormant, a 5% year over year increase. This essentially means there’s a bomb in your data, and you don’t know when it was planted or when it’s going to explode.
You need data resiliency to protect against ransomware
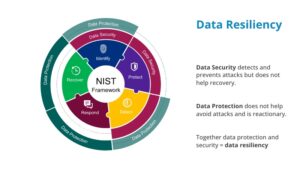
The only way to protect yourself against the worst-case scenario is with data resiliency. But what exactly does that mean?
Data resiliency is a combination of data security and data protection. There’s a fine distinction between the two, and only by combining them can you achieve what the NIST Cyber-Resilient Systems Framework recommends as a best practice.
Data security detects and prevents attacks, but it does not help with recovery. This branch of data resiliency includes things like automated patch management, a 24/7 security operations center, and endpoint security. Data security is how you prevent hackers from gaining access to your IT systems in the first place and how you know when they’re trying to break in.
Data protection, on the other hand, is reactionary. It doesn’t help you prevent attacks, but it helps you recover after something does go wrong. This could take the form of cyber incident response or business continuity planning.
Separately, data security and data protection are valuable but incomplete solutions. Only by combining them can you achieve true data resiliency.
Disaster recovery vs. cyber recovery
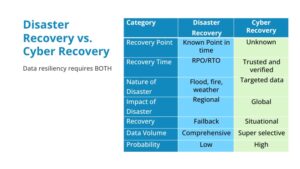
Looking specifically at data protection, you also need to understand the difference between disaster recovery and cyber recovery. You need both in order to make sure you have complete data resiliency.
The main difference is what kind of event you’re recovering from. If it’s a fire, a flood, or something similar, it’s disaster recovery. If it’s a ransomware attack or virus, then it’s cyber recovery.
The distinct nature of these events means they call for different approaches to recovery. For instance, a disaster happens at an identifiable point in time: you know exactly when the fire or flood occurred. But in the case of a cyber event, it can be hard to tell exactly when your systems were compromised.
First off, this means that in order to even get started with backups, you need to be sure you can trust and verify those backups. The last thing you want to do is reinstall the same virus that took you down. During disaster recovery, you don’t have to worry about your backups being infected, but that’s a real concern with cyber recovery.
Second, a disaster is usually a regional event. This limits the overall scope of the recovery. A cyber recovery usually takes place on a global scale.
If you want to know that your business can recover from any IT challenge, be sure to invest in both disaster recovery and cyber recovery.
The importance of immutable backups
As part of your long-term backup plan, especially for cyber recovery, it’s crucial to ensure that you’ve configured your backups to be immutable. This means they are impossible to delete or change.
One concerning thing we see is that bad actors will often go after backups before infecting a system with ransomware. Their goal is to make sure you have to pay the ransom; they want it to be impossible to restore the system without their key.
If your backups aren’t immutable, they’re basically useless for cyber recovery.
There are different types of immutable backups, ranging from policy-governed immutable snapshots to air-gapped cold data vaults, a.k.a. tapes. Your company’s approach to immutable backups ultimately circles back to a business discussion about what makes the most sense, especially when it comes to costs.
Recommendations to improve data resiliency

The first thing you need to understand is that data resiliency isn’t just about IBM i. It both affects and is affected by your entire IT environment, from networking to user endpoints. The challenges of data resiliency are magnified by the size of your environment; a bigger, more complex IT environment is harder to secure and protect.
One of the best things you can do to improve data resiliency is to replace aging hardware. If you’re stuck on old Power Systems, especially if they’ve reached end-of-life, then you’re basically a sitting duck. You may not be able to upgrade your operating system, which means you can’t update or patch your software applications.
As time goes on, more vulnerabilities are identified on those systems, and they stop receiving patches. Bad actors know about those vulnerabilities, and that’s the first place they’re going to look when trying to break in. Don’t make it easy on them!
Second, you need immutable backups for all the reasons we covered above. We can’t understate the importance of the word immutable here. If hackers can delete your backups, then they won’t do you any good.
Third, make sure you have both disaster and cyber recovery plans in place, and that both IT and business leadership are brought into the process. Remember, disaster and cyber recovery are not the same, and you need distinct plans for these different types of catastrophes.
Finally, do everything you can to harden your security. That could be as simple as tightening user access by not using default passwords or by making sure users don’t have too much authority. Way too often while CloudFirst is doing security scans for our clients, we find hundreds of users with all-object authority, the IBM i equivalent to root access. This is a huge vulnerability.
There’s so much more we could go into about cybersecurity, from mandating multi-factor authentication to realtime monitoring. Because there’s so much to address, we recommend doing a little at a time, putting one foot in front of the other. Then over time you can put it all together.
If you’re concerned about the cybersecurity of your IBM i, get in touch with CloudFirst today. We’ll run a security scan and provide you with a report to help you create a timeline for implementing a data resiliency strategy of your own.

